Managing your Salesforce org connections
In order to access your Salesforce metadata you need to connect (via OAuth) with one or more Salesforce orgs.
You can manage orgs both in your personal account, as well as (separately) for each team that you are a member of.
Connecting to a new Salesforce org
To add a new org, navigate to https://app.cirra.ai/mcp. You should see a page link this:
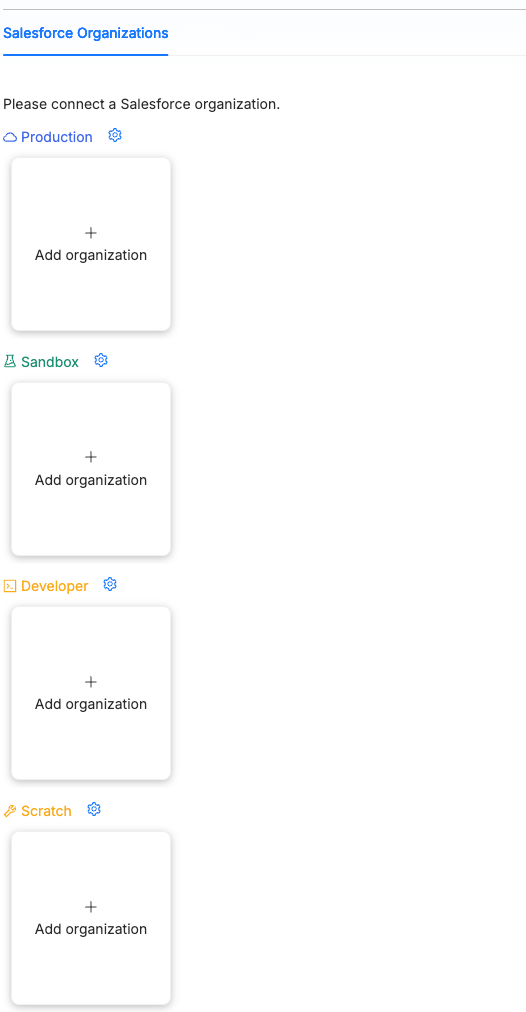
If you see a Verify your email address dialog, you need to first verify your email as described in Setting Up → Verifying your email address
Click on the "Add organization" button that matches the org type you want to connect to. In the dialog that appears enter a custom domain if applicable, and then click Submit.
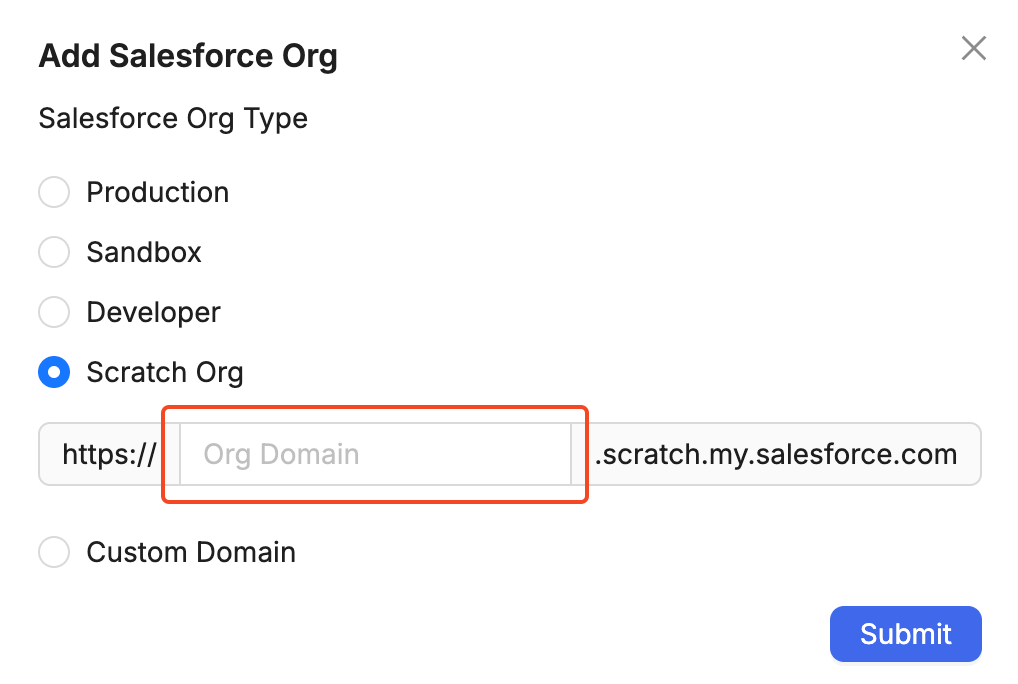
After entering your Salesforce login credentials you will be asked to authorize access to your org:
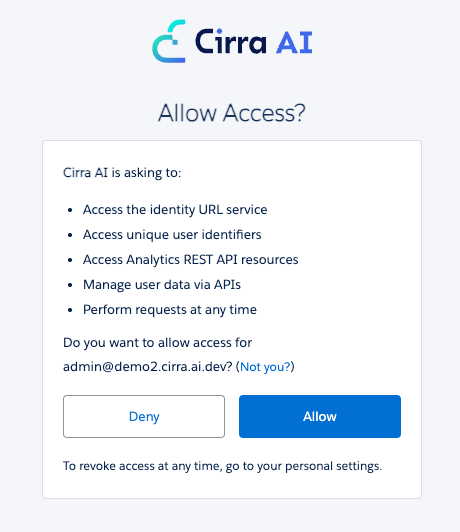
Note that we only ask for the minimum permissions required to manage your Salesforce org via the API. The OAuth credentials requested cannot be used to log into the Salesforce UI, only for access via API.
Clicking Allow should show a confirmation as follows:
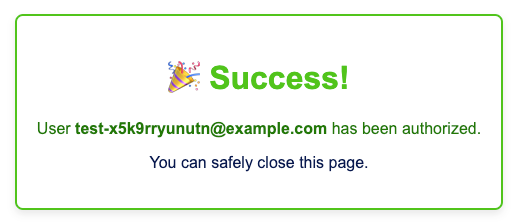
And the new org should appear:
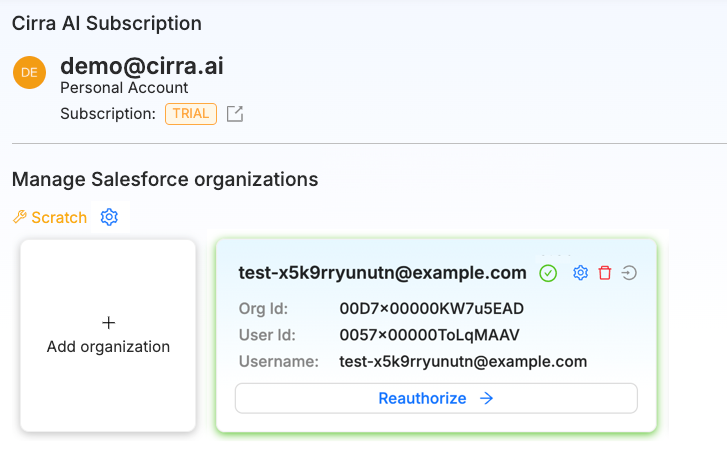
Cirra AI will act under the permissions of the user who granted the OAuth permissions, so it will only be able to make changes that the user would be able to make manually in the Setup UI.
See below under Access rights and security for more details.
If you are connecting to a recently created org, and you are logging in with a user that is not a System Administrator, you may receive an OAuth error (specifically app+must+be+installed+into+org) due the new Salesforce security measures recently rolled out around connected apps.
To resolve this you can either:
- Grant the user in question the Approve Uninstalled Connected Apps permission
- Either by adding that permission to an existing permission set assigned to the user, or creating a new permission set with that permission added
- Log in as System Administrator and explicitly install the Cirra AI app
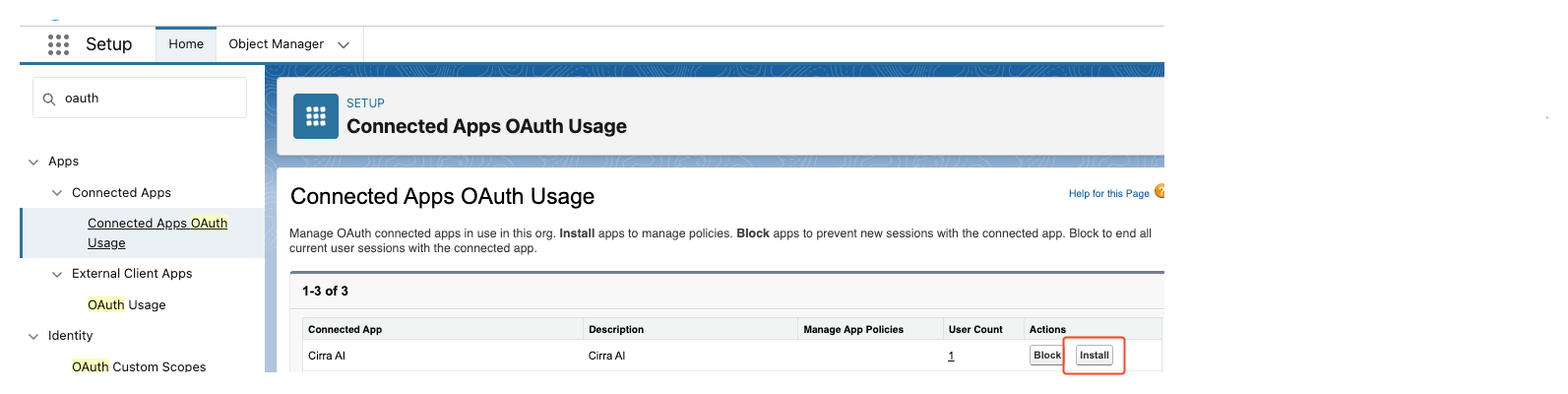
Details in: https://help.salesforce.com/s/articleView?id=005132365&type=1
Selecting the active org
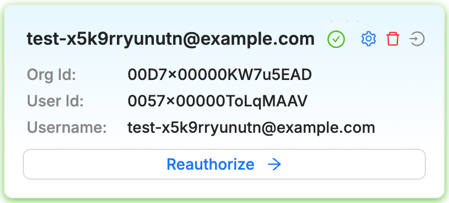
The MCP server can only interact with one org at a time. The active org is indicated by:
-
a green border if it has a valid OAuth connection
-
an orange border if the OAuth has expired
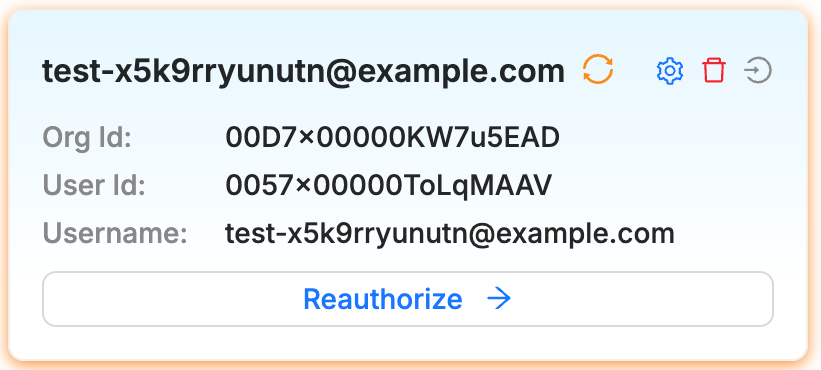
If the OAuth has expired you should click the Reauthorize button to attempt to refresh it.
To change the active org, click the Select button for the desired org.
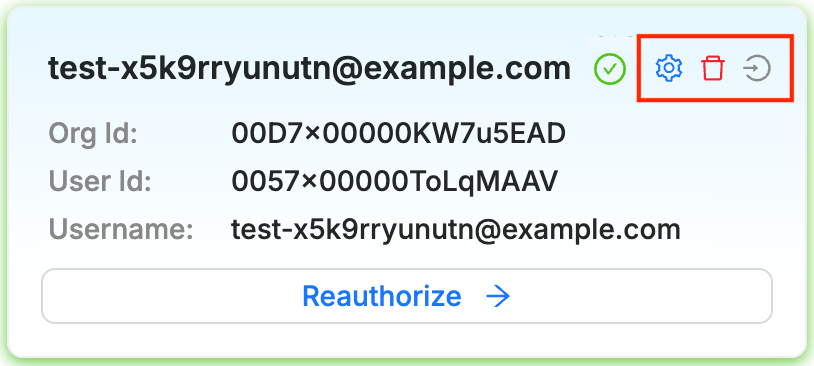
Managing orgs
You can use the icons at the top right of each organization card to:
- Manage the access rights settings for the org (see below)
- Remove the org connection
- Open the org (login may be required)
Access rights and security
It is critically important to carefully control access to your enterprise (meta)data. Cirra AI and Salesforce together provide multiple layers of protection:
- All access to Cirra AI is through OAuth with a Connected App
- No need to share your Salesforce user credentials with Cirra AI
- Cirra AI's access to your Salesforce org never is limiyted to that of the user you used to establish the OAuth connection.
- The OAuth user can be an API only user. In any case select a user with only the minimum required access.
- Salesforce provides numerous tools to control who has access to Connected Apps
- See the Best Practices section below
- Cirra AI allows you to further limit the access granted to orgs, or categories of orgs, to avoid exposing confidential information
Also:
- Cirra AI does not store or train on any (meta)data
- You can select an LLM provider that provides acceptable data privacy assurances
- Leading providers allow you to (at least) opt out of sharing your data for training purposes
- LLM clients typically require approval before any tool is called
Connected App best practices
In older Salesforce orgs, any Salesforce user with valid credentials can authorize a connection to the Cirra AI Connected App. In newer orgs access may be restricted (see https://help.salesforce.com/s/articleView?id=005132365&type=1).
Regardless, for maximum control in orgs with sensitive (meta)data, we recommend that you enforce restrictions on access to the Cirra AI connected app from within Salesforce.
The typical steps are as follows:
- System admin adds the Salesforce org to Cirra AI and authorizes it using OAuth
- After installation completes, admin logs into Salesforce and explicitly installs the connected app
- in Salesforce Setup, go to Connected Apps OAuth Usage, and click Install

- Set the OAuth policy to Admin approved users are pre-authorized
- Assign permission to use the app to specific users
- Most explicit is to create and assign a dedicated Cirra AI permission set (the set can be empty -- it's just used for this one purpose). But you can use existing permission sets too
- Assign the permission set(s) to any user who needs access

- Users who do not have the required permission set will not be able to connect to the org from inside Cirra AI
- in Salesforce Setup, go to Connected Apps OAuth Usage, and click Install
For full details on Connected App access controls, see the Salesforce documentation here
Cirra AI org-level access controls
On top of the security and control provided by OAuth and Salesforce, you can further limit the level of access to (meta)data in an org or categoy of orgs.
Access levels can be separately set for four categories of (meta)data:
- Metadata: all configuration, such as objects, fields, layouts, permission sets, profiles etc.
- User Data: users, groups, queues etc.
- Personal Setup Data: setup controlled by individual users, such as reports and email templates
- Business Data: Leads, Accounts, Cases etc.
For each of these access can be set at three levels:
- None: (meta)data can neither be read nor modified
- Read Only: (meta)data can be read, but not modified
- Read and Write: full access
Access can be restricted at two levels:
- The category of Salesforce orgs: production, sandbox, developer or scratch
- Each individual org
To configure these settings, click on the settings icon. This is available for each org category (Production, Sandbox etc) as well as the card for each individual org.
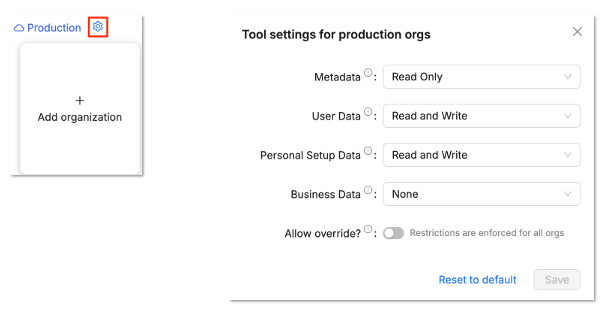
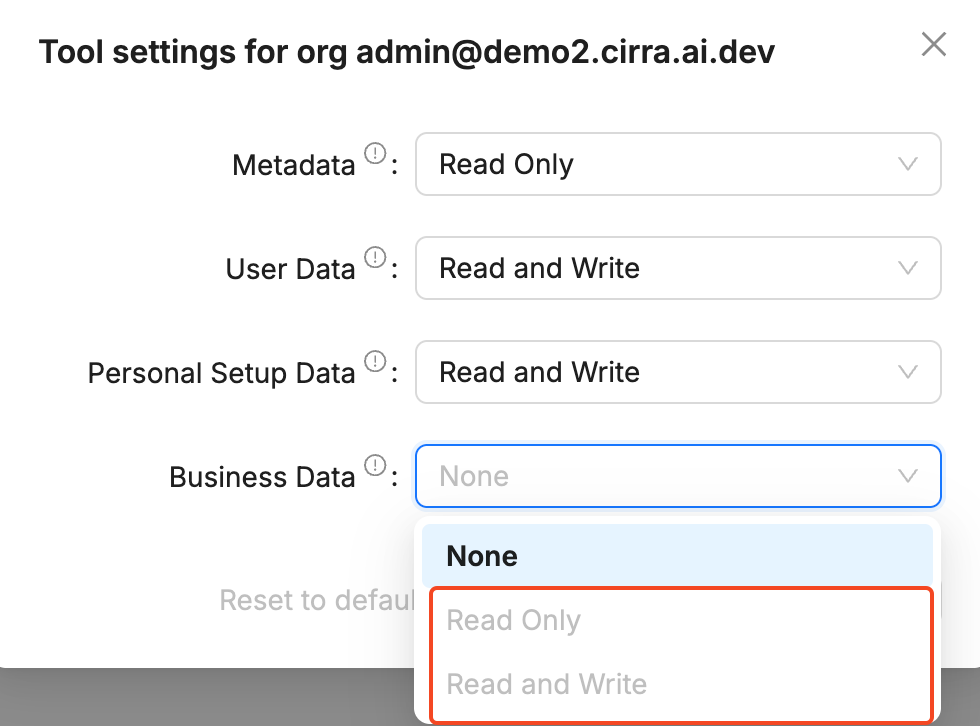
By default, individual org level settings can only be set to be more restrictive than category level settings. Less restrictive settings are disabled.
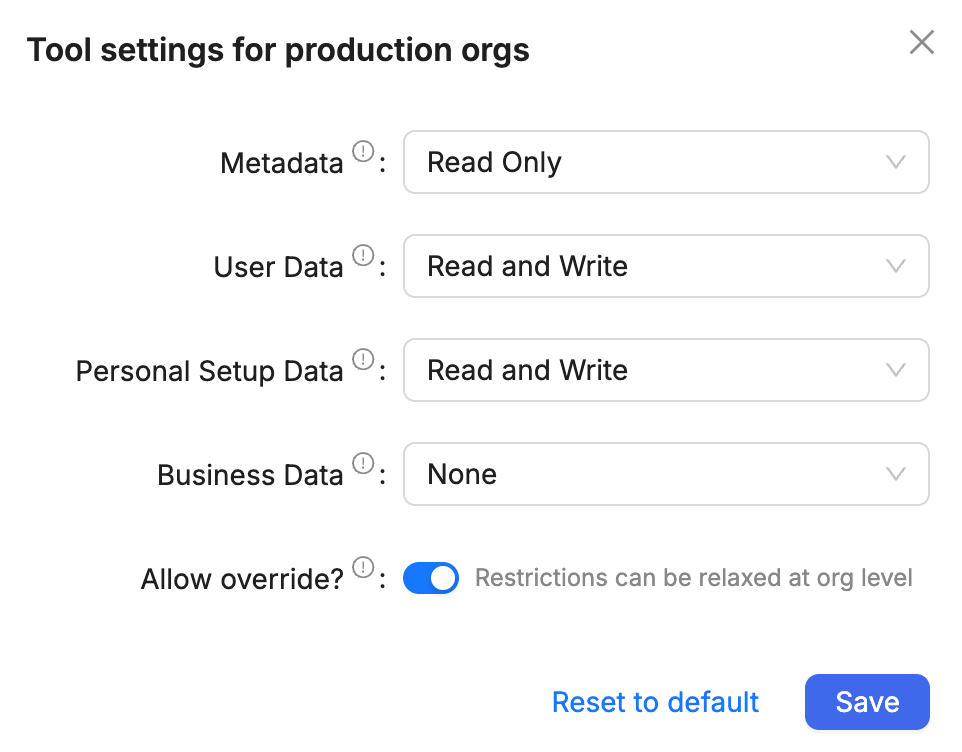
However, if you select the Allow override? option then individual orgs can relax the category-level settings
For Team accounts, category levels can only be set by owners or admins of the team.
To summarize, a user will have access to (meta)data in an org only if all of the following are true:
- The user who connected the org (via OAuth) has access
- The org category settings allow access
- Unless Allow override? is enabled
- The individual org settings allow access